Create an account
- Sign up at https://app.theswarm.com
- During onboarding, add your company’s LinkedIn URL to activate the AI Network Mapper, which maps your team’s network.
- After onboarding, you’ll get a 14-day free trial of our Premium plan, including API access.
- Add your connectors, team, partners, customers, investors, advisors, and search through everyone’s combined networks. The Swarm Relationship Strength Score automatically evaluates connection quality.
- Explore plans and pricing to find the best fit for you.
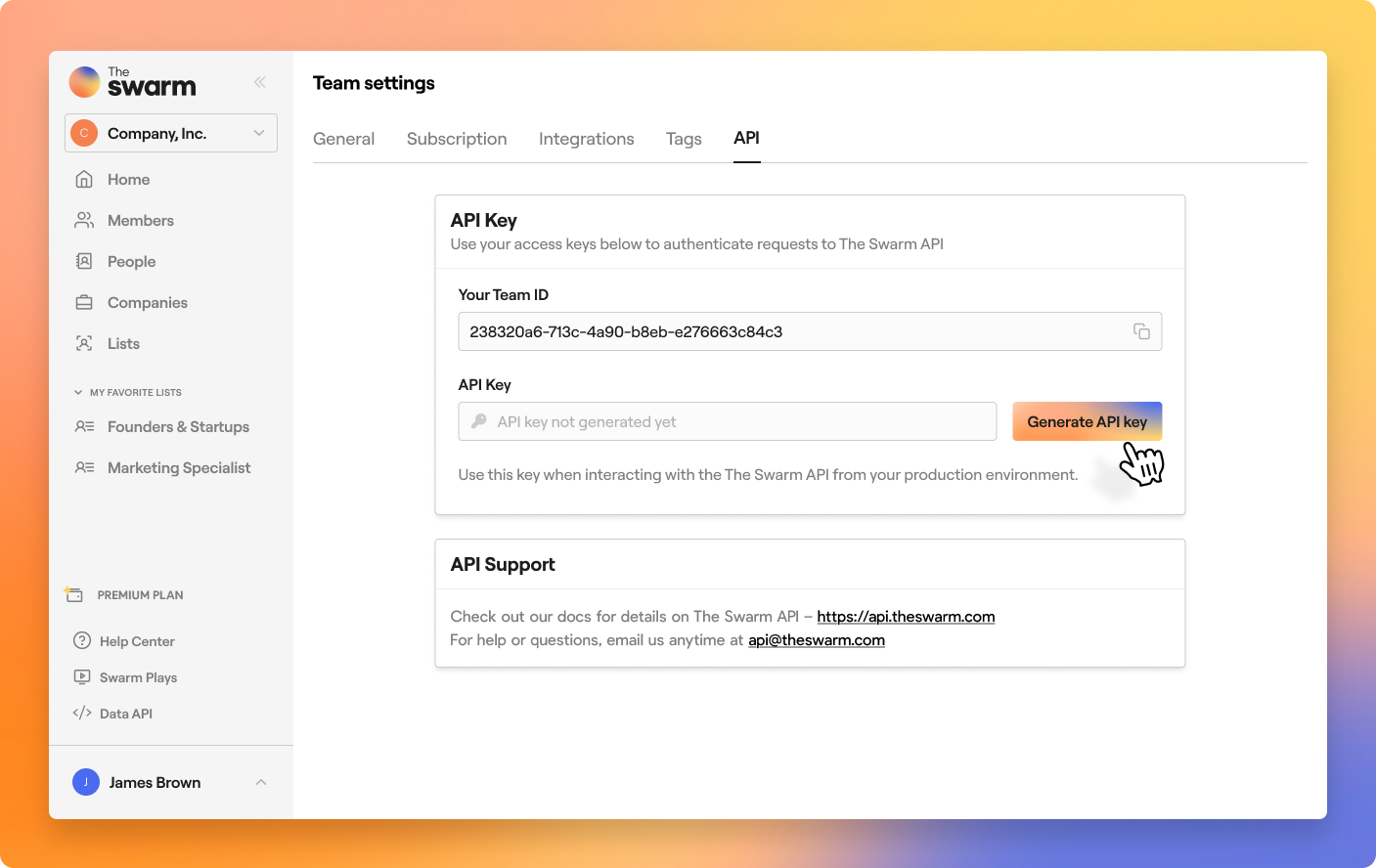
Get Your API Key
- Navigate to Team Settings by clicking your Team name in the top-left corner of the sidebar.
- Go to the API tab.
- Click Generate API Key to create your key.
- Copy the generated key to your clipboard for use.
Using Your API Key
Include your API key in the headers of each request by adding it as thex-api-key header. This authenticates your API calls and allows access to Team-specific data, such as profiles, lists, and tags.
Security Best Practices
Your API key is a powerful credential—treat it like a password:- Keep it private: Never share your API key in public spaces, such as GitHub or client-side code.
- Protect your access: Unauthorized use of your API key can compromise your data and system integrity.
- Start small: When using the API, we suggest testing with a small batch of inputs first. This allows you to validate your setup and ensure everything works smoothly before scaling your processes.
- Rate Limits: Be mindful of rate limits to avoid unnecessary throttling (learn more here).
Encoding Standard
In our systems, URLs are always stored and returned encoded. Characters not allowed in standard URLs (e.g., spaces, special characters, emojis) are encoded using the%<hex> format. Slugs are stored, returned, and sent in requests decoded, exactly as entered by the user. It is recommended to use encoded URLs and decoded slugs in all requests.